In recent years, a rise in Internet banking and mobile banking often goes together with the development of cybercrime. How do hackers stay ANONYMOUS?
Hackers cover their footprint in some ways and try to steal valuable information to earn money. This article will give you helpful information about discovering the appearance of an unwanted guest. Start your journey right now!
How Do Hackers Hide Themselves?
Hackers could use five main effective methods to stay anonymous online. They can use VPN or Tor, hide their MAC addresses, use no-tracking search engines, send anonymous emails, or use remailers.
1. Use VPN
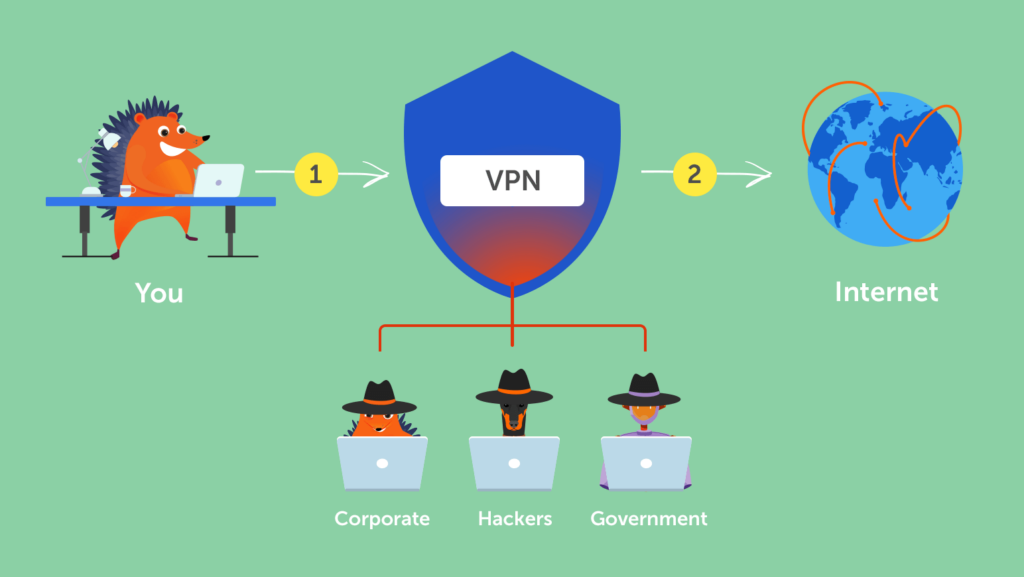
We can quickly discover hackers’ traces if they connect to the Internet directly.
VPN (Virtual Private Networks) can prevent third parties from tracking down their IP address (Internal Protocol address), locating their positions, and gathering personal information.
A VPN can help hackers remain anonymous by faking their IP addresses. So the authorities, the ISP (Internet Service Provider), or any other third parties can only find the IP addresses of an encrypted VPN server.
2. Use Tor
Tor (The Onion Router) can conceal users’ IP addresses by bouncing web traffic via many routers called nodes. After going through these nodes, websites and other parties cannot pinpoint their exact location geographically.
There are also various other benefits when using the Tor browser. Tor clears browsing history, and cookies help hackers stay anonymous online.

Tor and VPN can both hide hacker identity, and a combination of VPN and Tor will be the best option.
Hackers let VPN mask the IP address before using the Tor network, so even if Tor fails, their identity still remains secret.
You can illustrate that VPN can help hackers hide their location while Tor keeps the way to reach it secret.
3. Hide MAC Addresses
Each smartphone, computer, or other electronic device has its own MAC address as an ID number. They could not access the Internet or function properly without a MAC address.
While a MAC address identifies the electronic device itself, an IP address identifies the internet connection of this device. They help to track its online location.
Hackers can hide their identity by changing MAC addresses and masking IP addresses.
4. Use No-Tracking Search Engines
Unlike us, a professional hacker will never use Google or Bing. They prefer search engines like Brave and DuckDuckGo, which don’t record their IP addresses, cookies as well as browsing data.
5. Send Anonymous Emails or Use Remailers
An anonymous email allows senders to hide all their identity as it doesn’t reveal any personal information, IP address, name of the device, or even when we sent the email.
Remailer service acts as an intermediary. It will forward your email anonymously from your address before reaching the recipient.
Hackers can send data without exposing their identity by using anonymous email and remailer services.

What Do Hackers Want When They Hack?
There are several goals they share in common, including earning money, stealing information, spamming, and other purposes.
1. Money
Undoubtedly, many hackers are willing to commit cyber crimes because of money. Large organizations are their potential victims. They collapse the computer system and require companies to pay a ransom.
They also attack individual accounts and try to conduct financial transactions like applying for a massive loan or transferring money.
2. Information
Another reason why hackers hack is to steal your personal information. Then they can sell it to earn money.
For example, advertising companies are willing to pay an exorbitant price to build their customer database and understand customer behavior.
3. Spamming
Some hackers will access your Internet browser and force you to watch unwanted ads. If you accidentally click on these ads, they can hack your social media and email to spread spam for some particular purpose.
4. Other purposes
At the same time, many hackers aim at other purposes instead of money or your information. Hackers sometimes desire to attack a specific website just to show their different views on politics, religion, or moral issues.
Other hackers shut down a system just for fun, to gain knowledge, or boost their self-esteem. For them, hacking is a hobby and an addiction.
Should I Be Worried If Hackers Have My IP Address?
An IP address doesn’t contain sensitive personal information like your identity, phone number, or geographic location. It is still worth being worried if hackers have your IP address.
Hackers can dig into your IP address to get valuable information in some ways. For example, they can use your IP address as a starting point to find your location and disturb your privacy.
Based on your IP address and spooning on your social media, hackers can get information about your geographic location and understand your habit. They can rob your house and cause actual monetary loss for you.
How Do You Know If A Hacker is Watching You?

Hackers are excellent at hiding their identity. They seem invisible to you. So how do you know if a hacker is watching you?
There are several symptoms you should take into consideration.
- Traffic redirects: You find some strange website addresses on your browsing history, or your browser is running when you don’t open it
- Annoying pop-ups: You constantly receive pop-ups that you haven’t seen before. They often introduce new products or services.
- Malware in your browser: You discover some sudden appearances of add-ons, browser toolbars, or even software.
- Account takeovers: Your password became invalid, and you cannot log into your account. Someone has stolen your information and changed it.
- Unstable Internet: The Internet connection suddenly becomes slow, and sometimes you cannot access the Internet.
- Collateral damage: Your family members and friends told you they had received weird messages or emails. Hackers already have access to your account and stole your contact.
- Fake cautions: You receive warning messages that viruses are attacking your system, and you should install new software to protect your device.
- Uncontrolled mouse pointer: Of course, there might be a technical issue.
But if there is nothing wrong with your mouse, chances are hackers have already attacked. Your mouse pointer makes precise movements to its destination, and you can’t control it anymore.
How Do Hackers Get Caught?
Hackers can adopt various methods to hide their identity. Catching cyber criminals seems like catching smoke with bare hands.
However, humans make mistakes, and hackers are not an exception. They will reveal themselves by creating careless mistakes. Police can exploit their carelessness and discover who they are in real life.
Hackers often use the same malicious software to attack different companies and individuals. By summarizing and analyzing potential evidence, police can determine their geographic location and identity.
Many hackers only concentrate on achieving notoriety. As a result, they will brag about their success on hacker forums. For police, it may be a warning sign of the existence of some wrongdoers.
Wrapping Up
Hackers will make every effort to hide their identity and cover their tracks. They will use VPN, Tor, or other measures to remain anonymous online and escape the law’s punishment.
However, there are many ways that police can track down and bring them to justice. And we should be aware of their existence and protect ourselves from being their next target.
